To successfully install Anaconda Server, you must have already prepared your environment according to the Standard environment preparation topic.
Installing Anaconda Server
-
Download your installer by running the following command:
-
Run one of the following installation commands. Choose the command that corresponds with your setup.
The installation process creates two distinct user profiles: one for administrating Anaconda Server and one for administrating Keycloak. Login credentials for these profiles are shown during the installer output. Use these credentials for your initial login, and update them as soon as possible.
- HTTP
- HTTPS
- Grafana monitoring
- External Postgres and Redis
Example output
The installer directory contains both the installation script (install.sh) and thedocker-compose.ymlfile, which defines how the Anaconda Server services are run.
By default,/opt/anaconda/repois the file path for the installation folder. You can either create the folder manually by assigning write access to the current user, or use the-b(--base-install-dir) parameter to specify the folder for your installation.Never delete the directory containing thedocker-compose.ymland.envfiles.
Verifying your installation
Services are one-to-one to containers. Therefore, verifying that all major containers are up and not restarting or failing is a good first step.-
Return to your terminal and run the following command:
You should see output similar to the following:
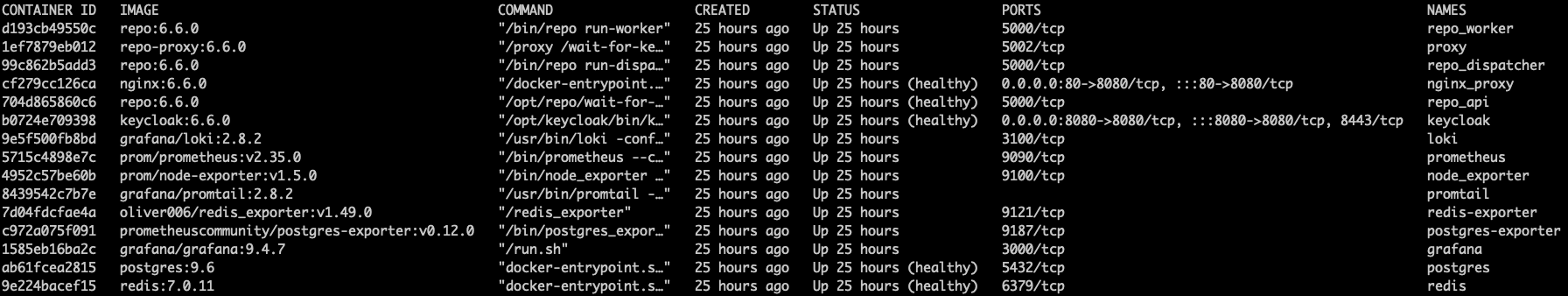
-
Verify that the following containers appear with a
STATUSofUp(not stuck in a restart loop) in the output:Additional containers
These containers should always be running. However, you might see additional containers, depending on the phase of installation or your initial configuration choices: - Open a browser and navigate to the domain that you supplied when executing the installer. If you are able to successfully authenticate and are asked for a license, Package Security Manager has installed successfully.
Advanced options
Further installation options can be seen by running the following command:| Arguments (shorthand) | Arguments (longhand) | Description |
|---|---|---|
-r DOCKER_REGISTRY | --registry DOCKER_REGISTRY | Docker registry, url:port (default uses the system Docker daemon) |
-h POSTGRES_HOST | --pg-host POSTGRES_HOST | Postgresql host (default is on internal Postgres instance) |
-p POSTRES_PORT | --pg-port POSTRES_PORT | Postgresql port |
-u POSTGRES_USER | --pg-user POSTGRES_USER | Postgresql user |
-pw POSTGRES_PASSWORD | --pg-password POSTGRES_PASSWORD | Postgresql password (will set the internal Postgres instance password) |
-e REDIS_URL | --redis REDIS_URL | Redis URL (default is an internal Redis instance) |
-d DOMAIN | --domain DOMAIN | External domain (or IP) of host system |
-c TLS_CERTIFICATE | --tls-cert | Path to TLS certification file for optionally configuring HTTPS |
-k TLS_KEY | --tls-key TLS_KEY | Path to TLS key file for optionally configuring HTTPS |
--default-user DEFAULT_USER | Default user name | |
--custom-ca-cert CA_CERTIFICATE | Path to custom CA certification, which should be respected | |
--custom-cve-source CVE_DEFAULT_MIRROR | For Airgaped environments provide a custom source for CVE data | |
--upgrade-from PREVIOUS_DIR | Previous install folder | |
-l | --no-image-load | Don’t load Docker images |
-y | --no-prompt | Answer yes to all prompts |
-- help | Print help text |