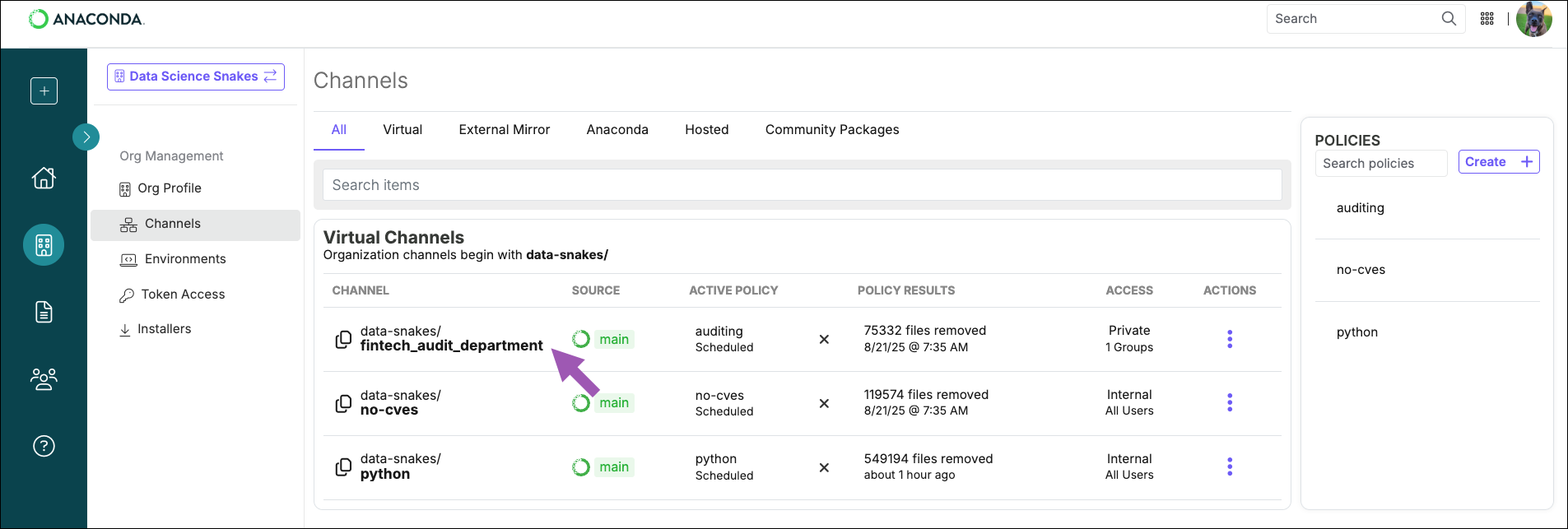
Searching for packages
If you want to know if a package is available on one of your organization’s channels, search for it by entering the package name into the Search artifacts field.If you see that the package contains zero files, it means that all the files for that package were removed from the channel, and the package is not available. Select the package to view the reason the files were removed.
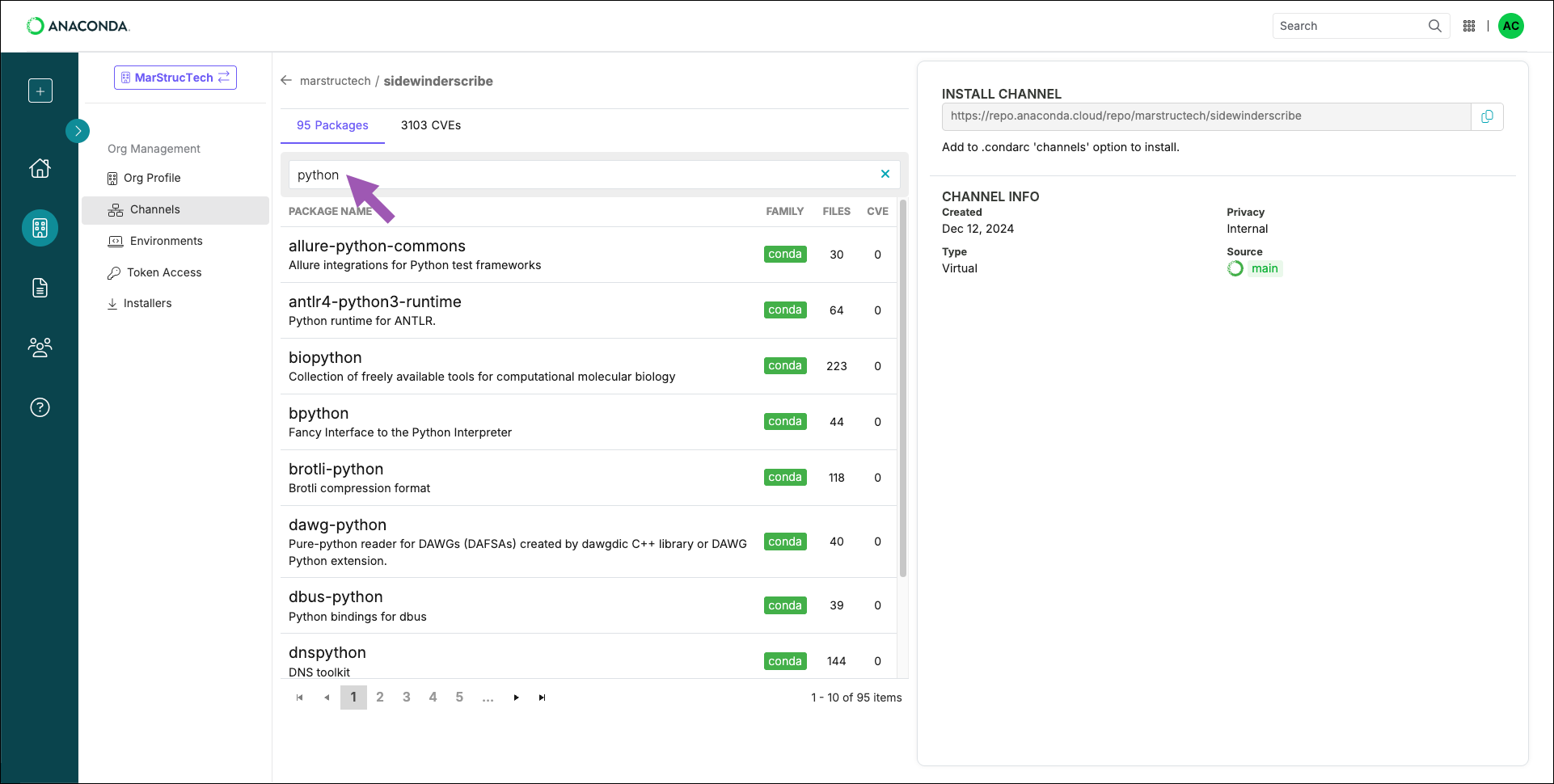
Viewing package details
Clicking on any package in a channel will display the package details. From here, you can view the following information:- All the files contained within the package
- The package’s dependents (other packages that require this package to operate properly)
- The package’s dependencies (other packages that this package needs to operate properly)
- that are associated with files in the package (for Business plan organizations)
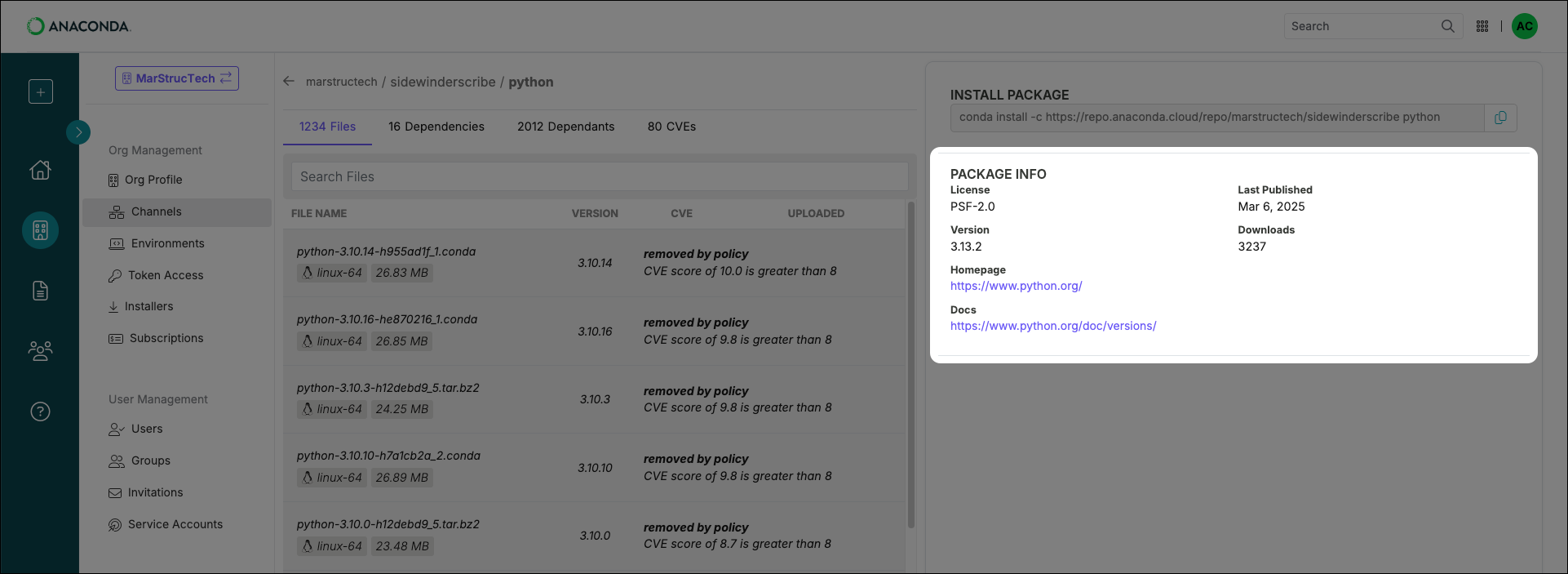
Package signatures
Packages in Anaconda’s come with a security signature: a special key value that proves that the package hasn’t been tampered with since going through Anaconda’s curation process. Files within a package that have a signature display a green check beside their names. The actual signature value can be viewed at the bottom of the metadata file.Viewing package metadata
From the package details view, click on a file’s name to display its metadata. The metadata is a.json formatted file that contains all of the information about the package file.
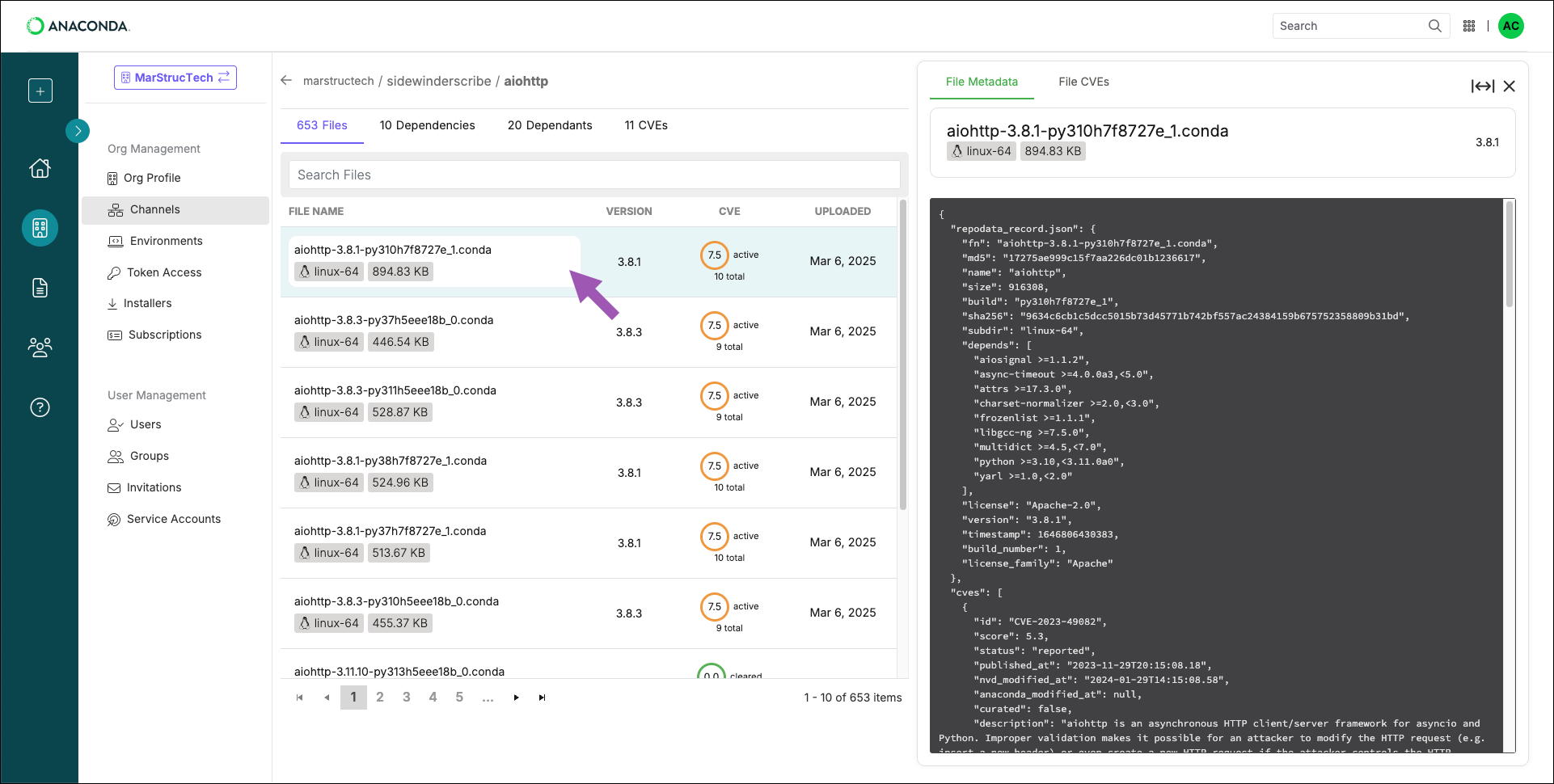
Viewing package SBOMs
Anaconda’s Software Bill Of Materials (SBOMs) are built in accordance with Software Package Data Exchange (SPDX) specifications, version 2.2.1, which specifies the checksum hash values of software down to the individual file level. From the package details view, click on a file’s name, then select the File SBOM tab.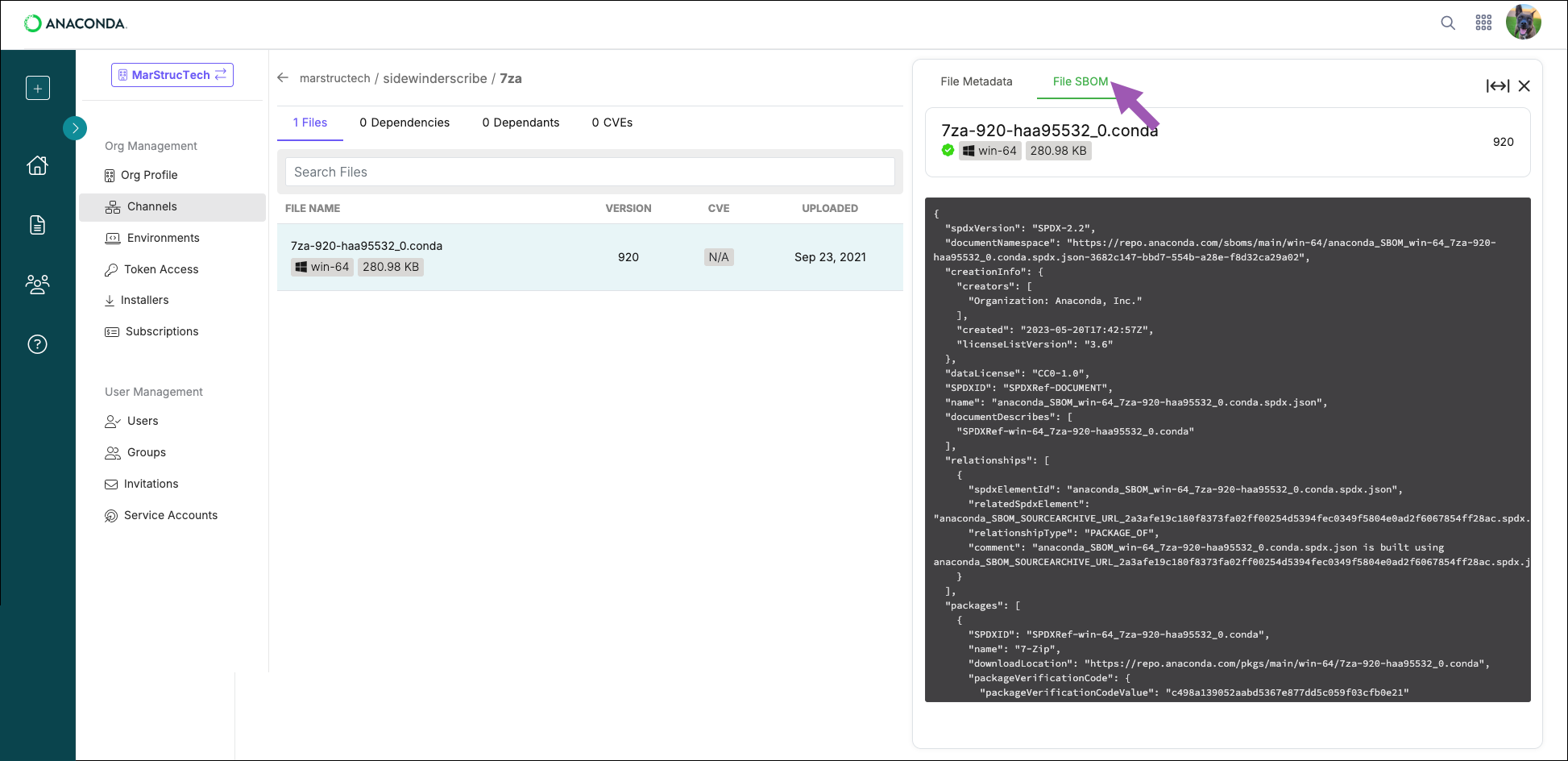
If no SBOM tab appears, there is no SBOM for that package file.
Installing a package in your environment
The package details page also provides you with a command to run if you want to install the package from this channel. Keep in mind that the command also installs the package’s dependencies.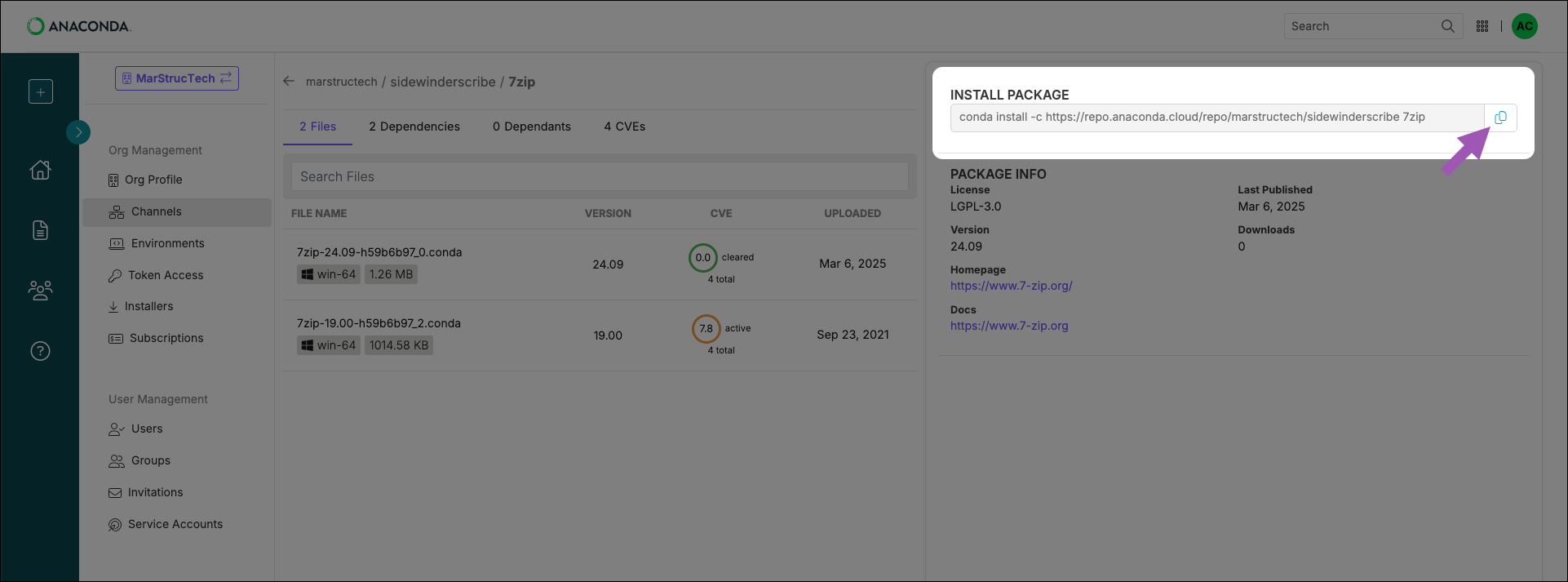
Conda package signature verification
The conda signature verification feature—available to users with paid access to our premium repository—allows you to detect tampering with packages and package metadata that took place between our secure build process and the end user’s install process. Based on The Update Framework (TUF), it provides defense against a wide variety of attacks. Please see our blog post on conda signature verification for more information.Enabling conda signature verification
-
Install the necessary packages:
-
Use
conda-tokento configure access, turn on signature verification, and empty the index cache:Replace <TOKEN> with your organization access token.
If no signatures are currently provided for a package (for example, if you are installing from third-party channels), the signature status message is not provided.
Example result
Example result